SQL Injection – “Let’s dump the database”
What is SQL injection?
✔ SQL injection is a code injection technique that uses malicious SQL code to access information/data that was not intended to be displayed. It can be used to obtain unauthorized access to the underlying data, structure, and DBMS.
✔ SQL Injection attacks are one of the oldest, most prevalent, and most dangerous web application vulnerabilities. The OWASP organization lists injections in their OWASP Top 10 2017 document as the number 1 threat to web application security.
✔ SQL injection vulnerability occurs when the application sends user input to the interpreter without sanitizing it and user input can be used to query database. SQL queries are used to execute commands, such as data retrieval, updates, and record removal.
Types Of SQL Injection Attacks :
SQL Injection can be classified into three major categories
- In-band SQL Injection
- Inferential SQL Injection
- Out-of-band SQL Injection
1) In-band SQL Injections
When the attacker uses the same communication channel to launch their attacks and to gather information. It is most common and easy-to-exploit.
There are two main types of In-band SQL injections :
(i)Error-based SQL injection - The Error-based SQLi attack depends on the error message thrown by the backend database server. The attacker performs malicious actions or injects invalid input which that could cause the database to throw technical error. These error messages are then potentially used to collect information about the database structure. When exploiting an error-based SQL Injection vulnerability, attackers can retrieve information such as table names and content from visible database errors.
Error: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''' at line 1 Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /hj/var/www/listproducts.php on line 74.
(ii) Union based SQL injection - This technique leverages the UNION SQL operator. UNION combines two or more sql statements and run them simultaneously in a single command. The attacker executes several selected statements as a single request which in return provides more information than intended as an HTTP response.
2) Inferential SQL Injection(Blind SQL Injection)
When the database server throws no errors/data on executing the SQL statement crafted with payload. The attacker tries to analyse the response and behavioural patterns of the server and this is called Blind SQLi because attacker can’t see any information in-band.
There are two types of Blind SQL Injection :
(i) Boolean-based Blind SQL Injections - The type of SQL injection attack where the database server returns a boolean output upon executing the SQL payload ie true or false. Depending on the result, the information within the HTTP response will modify (FALSE) or stay unchanged(TRUE). The attacker can then enumerate the database details further by the following the same process.
(ii) Time-based Blind SQL Injections - Time-based techniques are often used to achieve tests when there is no other way to retrieve information from the database server. It relies on sending an SQL query to the database which forces the database to wait for a specified amount of time (in seconds) before responding.
The response time will indicate to the attacker whether the result of the query is TRUE or FALSE. even though a vulnerable SQL query does not have any visible effect on the output of the page, it may still be possible to extract information from an underlying database.
3) Out-of-band SQL Injections
- Out-of-band SQLi is performed when the attacker can’t use the same channel to launch the attack and gather information, or when a server is too slow or unstable for these actions to be performed.
- These techniques count on the capacity of the server to create DNS or HTTP requests to transfer data to an attacker.
- This form of attack is primarily used as an alternative to the in-band and inferential SQLi techniques. Attackers may use this method if an injection does not occur directly after supplied data is inserted, but at a later point in time.
1. HTTP Query String Parameters (GET): Input parameters sent in the URL. The simplest form of SQL injection where the SQLI payload is transmitted as part of the URL.
http://testphp.vulnweb.com/artists.php?artist=-1 union select database(),version(),current_user()
(ii)HTTP Body Parameters (POST) - Input parameters sent in the HTTP body.
Payload : ' or 1=1--
(iii) HTTP Cookie Parameters - Input parameters sent in the HTTP cookie. Cookie parameter is vulnerable. The browser stores the cookie in a text file and is sent back to the server each time the browser requests a page from the server.
In below example target Cookie parameter is "login". The server responds with '200 OK' when the condition is TRUE {test/test' AND 1=1 AND 'x'='x} and '302 Found' when the condition is FALSE {test/test' AND 1=1 AND 'x'='y}.
(iv) HTTP Headers - HTTP request headers used by the applicatione. If the application stores HTTP header information in the database then it could be is vulnerable to header-based SQLi.
Injection point : Host | User-Agent | Referrer | Location | X-Forwarded-For
Automation of SQLi -
The SQL injection attacks can be automated using tool such as sqlmap and CO2 (Burpsuite extender).
Step 1: Check for vulnerability -
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -p cat
-u : URL to scan
-p : parameter to scan
* : Parameter to scan (if -p switch is not provided)
Step 2: List information about the existing databases -
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 --dbs
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart --tables
Step 4: List information about Columns present in a particular Table - sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart -T artists --columns
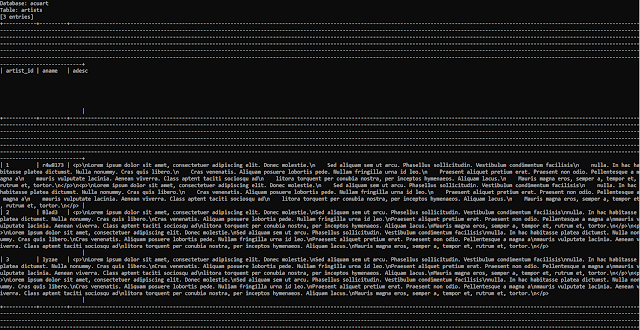
Step 5: Dump the Databse -
sqlmap -u http://testphp.vulnweb.com/listproducts.php?cat=1 -D acuart -T artists --dump
The impact of a successful SQL injection attack :
How to prevent SQL Injection?
1)Input validation -
- Validate all input data to the application using whitelist for input type, format and length.
- Use regular expressions as whitelist for structured data to ensure robust input validation.
- This method can only stop the most trivial attacks, it does not fix the underlying vulnerability.
2) Parametrized queries -
- Parameterized queries are a way to pre-compile SQL statements that force the developer to define all SQL code first, and then pass each SQL parameter to the query later.
- This allows the database to distinguish between code and input data, regardless of the user input supplied.
- SQL parameters are values that are added to a SQL query at execution time in a safe and controlled manner.
- Parameterized queries force the developer to first define all the SQL code, and then pass in each parameter to the query later. This coding style allows the database to distinguish between.
- Prepare once, execute many
- Prepared statements are already interpreted statements which ensures that an attacker shoould not able to change the intent of a query, even if SQL injection are inserted.
- For example - if an attacker enters 1 'or' 1 '= 1' as user ID in the login page, the prepared statement will literally check for the entire string 1 'or' 1 '=' 1.
- Stored procedures (SP) require the developer to group one or more SQL statements into a logical unit to create an execution plan. Subsequent executions allow statements to be automatically parameterized.
- Execute stored procedures uses safe interface such as Callable statements in JDBC or CommandObject in ADO.
- It enforce database management system (DBMS) to use character-escaping functions for user-supplied input.
- Escaping is the simplest way to protect against most SQL injection attacks, and many languages have standard functions to achieve this.
- To minimize the potential damage of a successful SQL injection attack, every database account associated with the application environment should be assigned least privilege and not the administrator-level privileges.
- Consider a web application firewall (WAF).
- A WAF operating in front of the web server monitors the traffic and identifies the patterns that constitute a threat.
- WAF can help stop most suspicious requests by looking for signatures (sequences of characters).
Thanks for reading 😊
Feel free to point out any mistakes or let me know if there is anything I should add 😊
Keep Learning, Keep growing 😊


















Comments
Post a Comment