XML Injection
XML injection is an attack technique used to manipulate or compromise the logic of an XML application or service.It allows an attacker to inject malicious and/or unexpected input that can break XML logic.
Depending on the functionality and XML usage of an application, a successful XML
injection may cause unauthorized access to resources and sensitive data disclosure.
What is XML?
✔ XML stands for eXtensible Markup Language.
✔ It is a markup language that defines a set of rules for encoding documents in a format that is both human-readable and machine-readable. It is designed to store and transport data. XML is extensible and hence can be tailored according to the application.
✔ XML uses a tree-like structure (XML Tree structure) of tags and data where tags can be user defined. To interpret XML data, an application needs XML parser, also known as the XML processor.
Example :
XML Entities :
XML entities are a way of representing an item of data within an XML document. There are two different types of entities external and lparameter entity, often shortened to external entity, that can access local or remote content via a declared system identifier.
Document Type Definition :
It contains declarations that can define the structure of an XML document, the types of data values it can contain, and other items. The DTD can be fully self-contained within the XML document (known as internal DTD) or it can be loaded from elsewhere (known as external DTD). The DTD is declared within the DOCTYPE element at the beginning of the XML document.
⏪Now going back to the vulnerability , XML injection is all about tricking the misconfigured and vulnerable XML parser to cause some harmful/unintended action.
Two well-known XML attacks are:
- XML Billion laughs attack
- XXE injection
1) XML Billion Laughs attack –
✔ Alternate Terms - XML bomb attack, XML Entity Expansion
✔ It is a DoS attack against XML parser that executes the XML payload recursively. This can lead to explosive growth of data/resource when parsed, causes denial of service.
✔ Example :
< <?xml version="1.0"?>
<!DOCTYPE lolz [ <!ENTITY lol "lol">
<!ENTITY lol2 "&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;">
<!ENTITY lol3 "&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;&lol2;">
<!ENTITY lol4 "&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;&lol3;">
<!ENTITY lol5 "&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;&lol4;">
<!ENTITY lol6 "&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;&lol5;">
<!ENTITY lol7 "&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;&lol6;">
<!ENTITY lol8 "&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;&lol7;">
<!ENTITY lol9 "&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;&lol8;">
]>
<lolz>&lol9;</lolz>
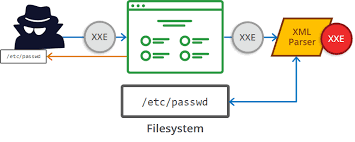
2) XXE Injection -
✔ XML External Entity Injection.
✔ XXE attack occurs when XML parser inadvertently leaks sensitive information. It allows an attacker to view files on the application server filesystem, and to interact with any backend or external systems that the application itself can access.
✔ Example : (pull data from the server's /etc/passwd file)
<?xml version="1.0"><!DOCTYPE test [<!ENTITY xxe SYSTEM "file:///etc/passwd" >]>
<test>&xxe;</test>
How to Test -
Step 1: Check for vulnerability
Insert XML metacharacters and look for any unintended output or exception. If the user input is not sanitized properly, the application will likely throw some error.
List of XML metacharacters :
- Single quote:’
- Double quote:”
- Angular parentheses: > and <
- Comment tag: <!, —, /→
- Ampersand: &
- CDATA section delimiters: <![CDATA[ / ]]> OR <![CDATA[]]>]]>
Step 2: Exploit the vulnerability using XML injection payloads
Impact of a successful XML injection attack :
- It can result in unauthorized access to sensitive information.
- Unauthorized deletion and modification of data
- Privilege escalation within the application
- Potential impact of XML injection depends on vulnerable application and its functionality. However, in a worst-case scenario this attack could result in full system compromise.
How to prevent XML Injection?
1)Input validation -
- Includes properly managing and sanitizing any external input.
- Application should validate user input before sending it to parser.
2) Block meta-charactes -
- It could be done by blocking some meta-characters such as < and >.
- Another option is to replace them with corresponding HTML character entities- such as < and >
- Configure the XML parser to disable inline expansion/inlining.
- For example - In .NET the default value for XmlReaderSettings.MaxCharactersFromEntities is 0 and means "no limit". By setting the MaxCharactersFromEntities property , one can limit the number of characters that can be created through entity expansions.
- Configure the XML parser to avoid resolving external references entirely. It is the simplest way to prevent XXE attacks.
- For example – set libxml_disable_entity_loader(true); (when using the default XML parser in PHP).
- For example - Use defusedxml libraries for XML parsing {for Python}
- Use Nokogiri libraries (in case of Ruby)






Comments
Post a Comment