XML Injection
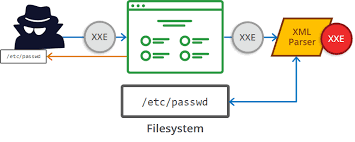
XML injection is an attack technique used to manipulate or compromise the logic of an XML application or service.It allows an attacker to inject malicious and/or unexpected input that can break XML logic. Depending on the functionality and XML usage of an application, a successful XML injection may cause unauthorized access to resources and sensitive data disclosure. What is XML? ✔ XML stands for eXtensible Markup Language. ✔ It is a markup language that defines a set of rules for encoding documents in a format that is both human-readable and machine-readable. It is designed to store and transport data. XML is extensible and hence can be tailored according to the application. ✔ XML uses a tree-like structure (XML Tree structure) of tags and data where tags can be user defined. To interpret XML data, an application needs XML parser, also known as the XML processor. Example : An XML document is always descriptive and can be referred as XML tree structure. XML Ent...

